Introspectus tests compliance against the updated November 2023 Essential Eight rules!
Have you assessed your
Essential Eight?
Be assured your Essential Eight security controls are effective. Introspectus Assessor is a security auditing tool that focuses on an organisation’s compliance with the Australian Cyber Security Centre’s Essential Eight.
Real-Time Assessment and Remediation Advice.
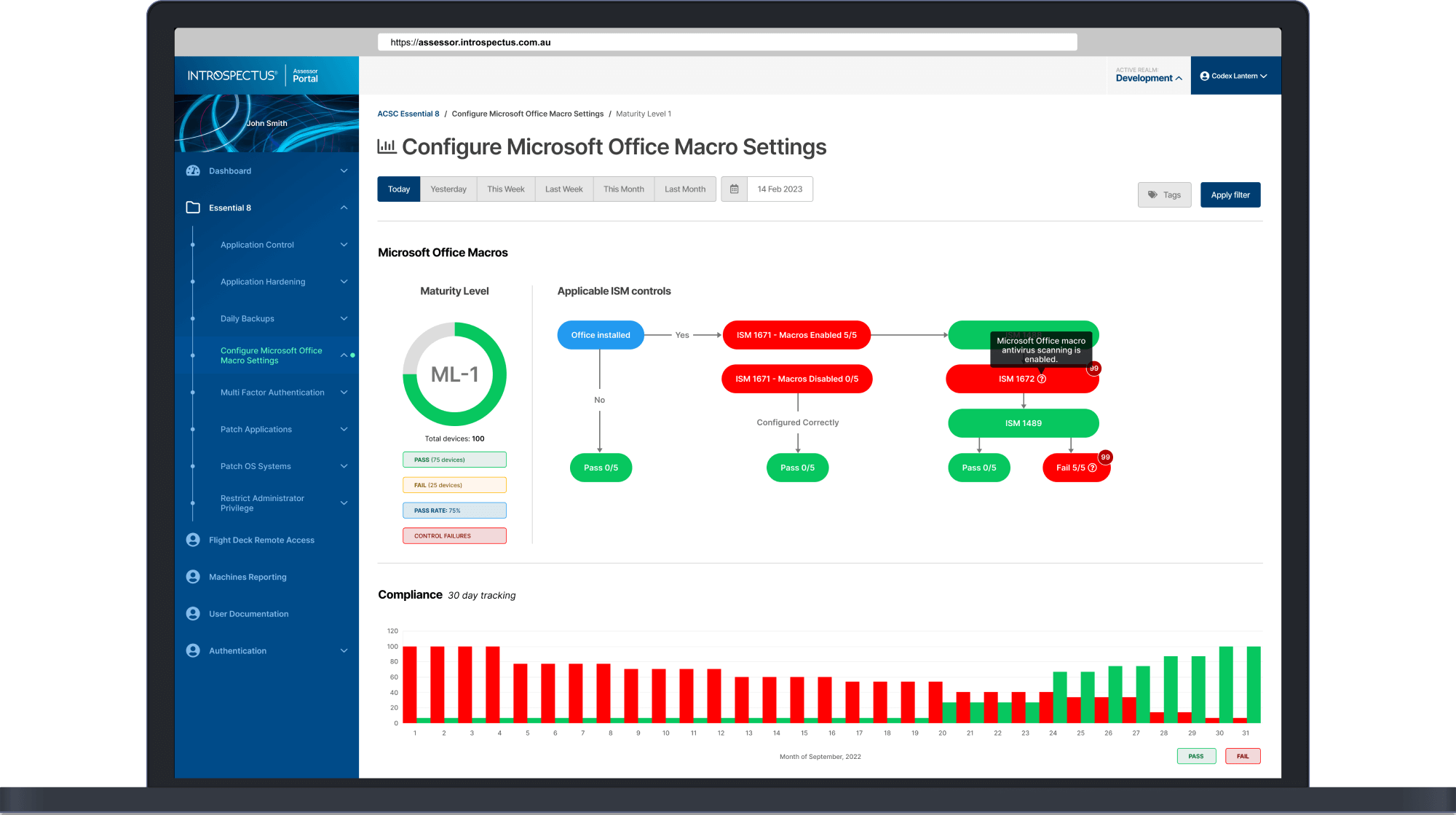
Introspectus Assessor audits the security controls on all endpoints and provides assurance that security controls are in place and working effectively across an organisation. Introspectus Assessor highlights failures in controls and provides advice for remediation.
Technical How-To
Implementing 1,000+ controls to ensure full Essential Eight compliance can be daunting. Introspectus Assessor highlights security failures with advice on how to fix them.
Real-Time Risk Assessment
Real-Time Executive and Board-Level reporting of your security posture measured against the Essential Eight Maturity Model.
Download a Limited Free Trial
A no obligation free trial of Introspectus Assessor gives insight into the capabilities and control gained from real-time reporting and technical advice to overcome any security gaps and improve your security posture.
for Windows 64bit

Frequently Asked Questions
Here is a selection of common questions about Introspectus Assessor and ACSC’s Essential Eight Maturity Model.
Essential Eight is a set of strategies to mitigate cyber security incidents. These eight primary mitigation strategies make it much more difficult for attackers to gain access to IT systems or processes essential to the operation of your business.
Introspectus Assessor is a security auditing tool that focuses on an organisation’s compliance with the ACSC’s Essential Eight.
Introspectus Assessor is made up of:
- Introspectus Assessor Agent (deployed to Microsoft Windows Devices)
- Introspectus Assessor Flight Deck (component of the Agent)
- Introspectus Assessor Portal
- Introspectus Assessor Advice Portal
Introspectus Assessor Agent has two modes of execution:
- Silently – where it performs security audits on a 12-hour schedule (which is configurable) and uploads results into the web-based Portal for analysis; and
- Using – which permits the execution of the application interactively form the device’s Windows System Tray, allowing real-time analysis of compliance against the testing rules.
Can’t find what you’re looking for? Visit our FAQ page